Discover, assess, and govern every non-human identity, from API keys to service accounts, with automated risk scoring, least-privilege enforcement, and full lifecycle governance.
of security leaders believe attackers are explicitly zeroing in on machine identities in cloud-native and developer environments
the ratio of Non-Human Identities (NHI) to Human Identities
of all identity-related breaches are attributed to hacked machine identities
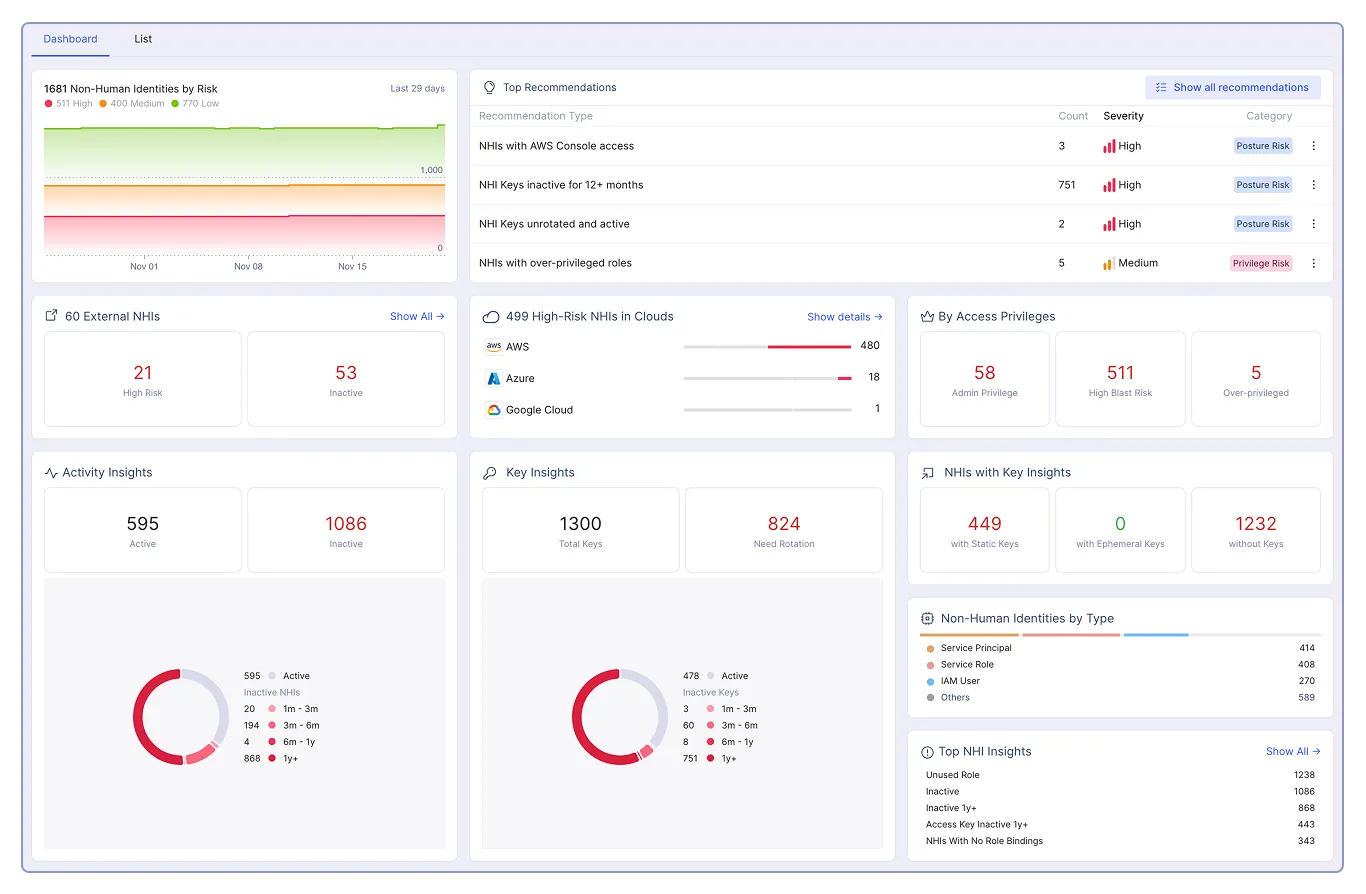
Centralized inventory of all NHIs and Keys with automatic classification by risk and usage context
Identify dormant, external, and high-risk NHIs and detect toxic combinations that increase risk
Detect inactive and unrotated keys and identify unusual activity patterns
When NHI Security manages includes entitlements and lifecycle, everyone wins






With Andromeda, we gained critical visibility into our NHI security posture, enabling us to effectively eliminate risks from inactive and overprivileged non-human identities, reducing our cloud attack surface and increasing our security posture.

With Andromeda, we gained critical visibility into our NHI security posture, enabling us to effectively eliminate risks from inactive and overprivileged non-human identities, reducing our cloud attack surface and increasing our security posture.

