Achieve Zero Trust by automating enforcement and continuously rightsizing permissions with unified identity data and intelligent analysis of activity data
the percent of entitlements that are granted but are never used
the percent of identities found to possess excessive privileges
the percent of permissions that are granted but not required for daily business operations

Centralized, granular visibility into every human and non-human identity access across cloud, SaaS, and on-prem
Understand how access is granted, whether directly, via groups, or inherited and lateral permissions
Quantify risk of access based on type of permissions, business criticality of the asset, and presence of sensitive data
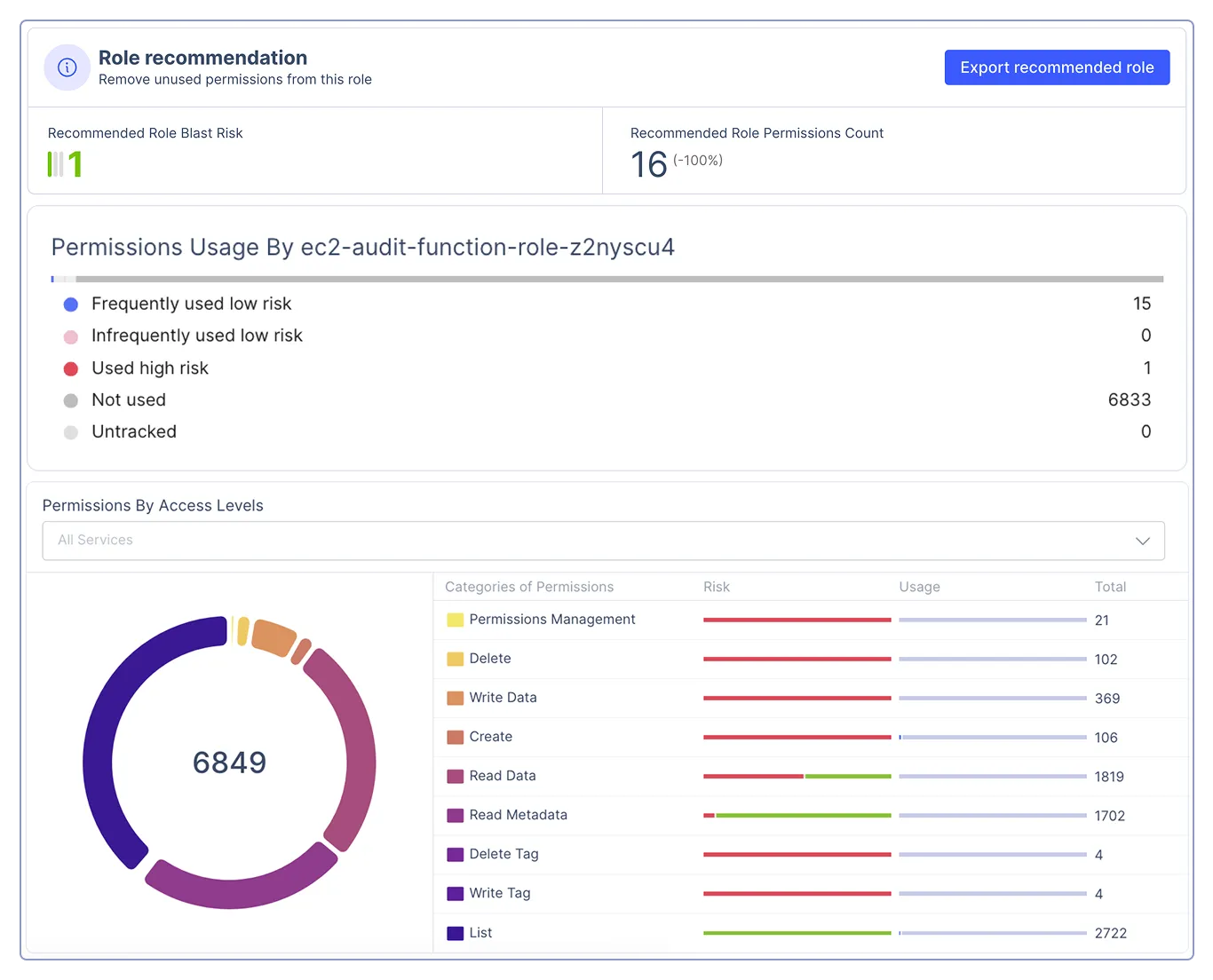
Real-time insights into granular usage—not just who has access to what, but who is using what, with insights into risk and usage frequency
Continuously analyze usage, behavior and privilege risk to remove unused roles and excessive permissions
Move high-risk roles to Smart Just-in-Time access
When you bring your organization closer to Zero Trust, everyone wins


.svg)

Our process is now centralized and fully automated with instant context for every access review request. This transformation has saved countless hours and empowered our security team to confidently enforce least privilege principles, ensuring that every user has only the access they need.

Our process is now centralized and fully automated with instant context for every access review request. This transformation has saved countless hours and empowered our security team to confidently enforce least privilege principles, ensuring that every user has only the access they need.
