Gain continuous visibility into who has access to what, and more importantly who is using what to reduce your risk across all environments.
of all breaches involved identities
the number of days it takes to detect and contain breaches initiated by stolen or compromised credentials
the time it takes from identity compromise to an attacker initiating lateral movement
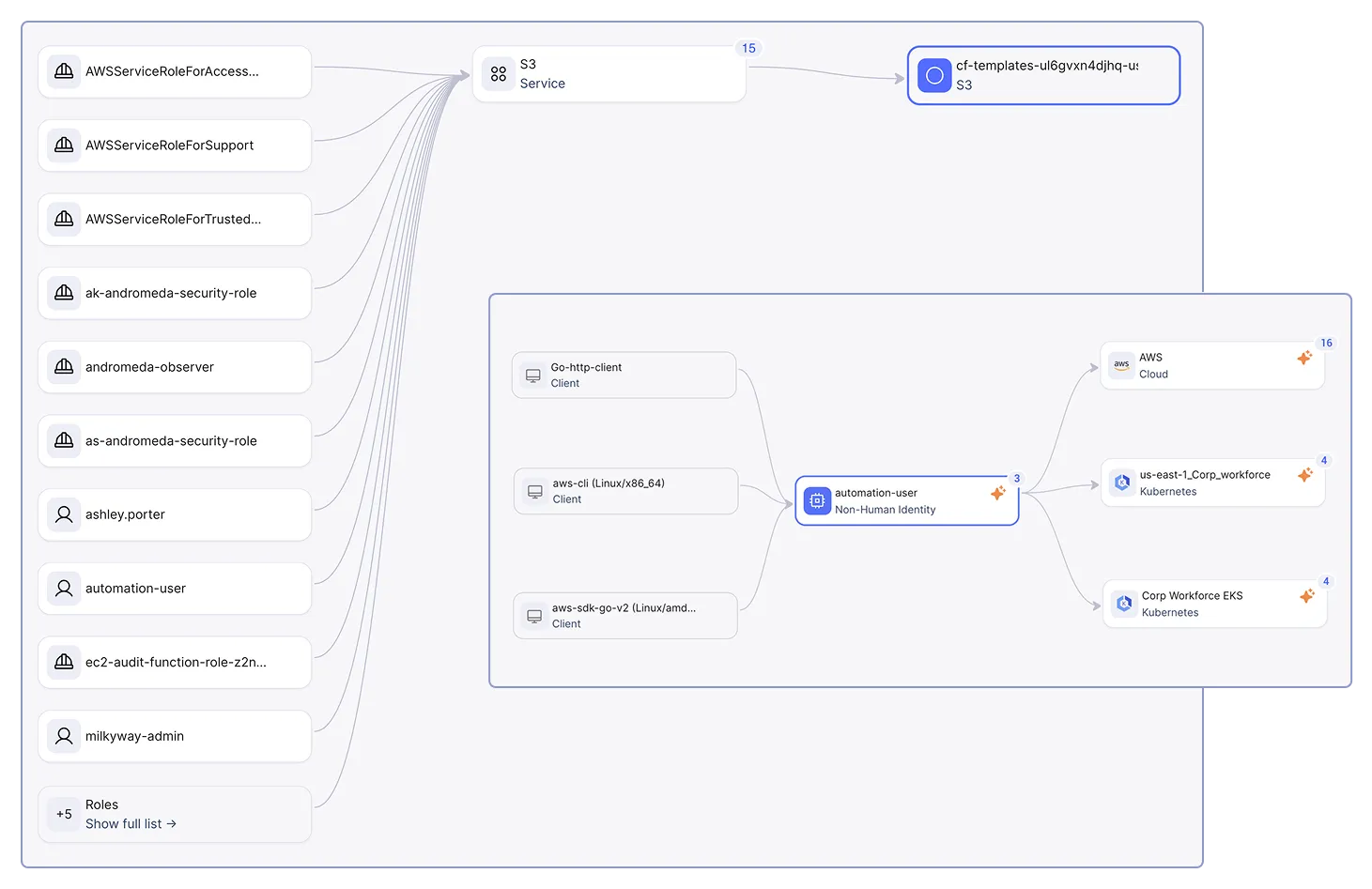
Complete visibility with deep context across every identity, human, non-human, and AI for continuous posture management across cloud, SaaS, and on-prem
Granular, deep insights from actual activity to know who (human or NHI) is doing what with their access
For high-risk identities and access: stale and dormant accounts, admin and excessive privileges, unused roles, external access, unrotated keys, etc.
Prioritize and remediate high-risk toxic combinations
Leverage usage and behavioral analytics to continuously right-size entitlements, removing unused or unnecessary permissions
Transform high-risk standing privileges into adaptive, time-bound access that scales across all identities
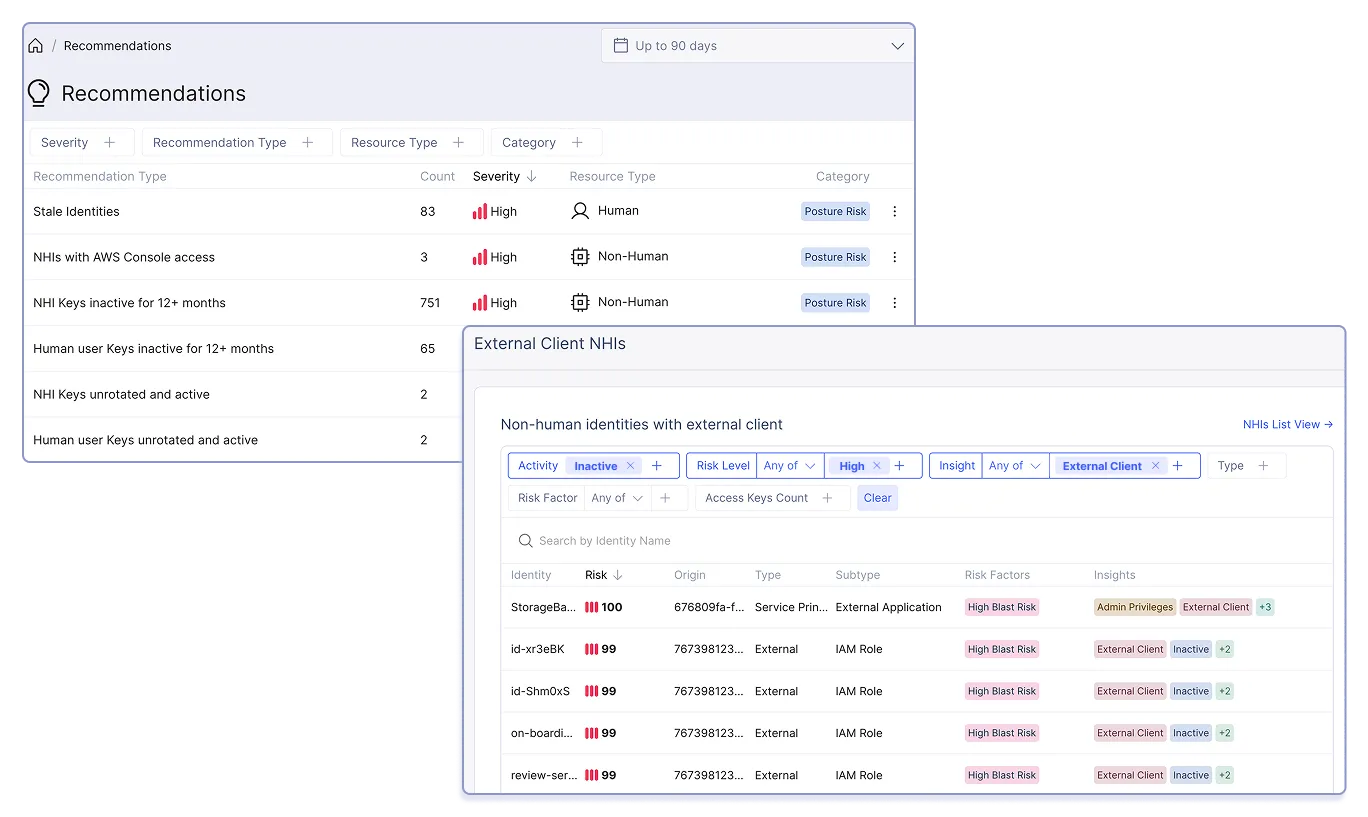
When you unify identity data everyone gains continuous risk intelligence


.svg)

.webp)
The single-pane-of-glass view of human and non-human identities is a game-changer for efficiency. Andromeda quickly provided the insights needed to right-size over-privileged roles and remove stale accounts. We now have full control and a clear path to advanced, proactive security with Just-in-Time access.

The single-pane-of-glass view of human and non-human identities is a game-changer for efficiency. Andromeda quickly provided the insights needed to right-size over-privileged roles and remove stale accounts. We now have full control and a clear path to advanced, proactive security with Just-in-Time access.

.webp)